Spectre and Meltdown CPU Vulnerability Test and Microcode Update on Linux
On this page
- How to check if your Linux server is vulnerable to Spectre CPU bugs
- Installation
- How to check Linux for Spectre and Meltdown vulnerability
- How to install/update Intel microcode firmware on Linux?
- How to install Intel microcode firmware on Linux using a package manager
- How to update/install microcode downloaded from Intel site?
- How to install Intel processor microcode blob for Linux (20180108 release)?
Introduction to Spectre & Meltdown CPU Vulnerabilities
One way to block these attacks is to empty the memory caches at certain times, eliminating exfiltrated information before the attacker can access it. Downloading the cache after each system call would probably block a wide range of speculative attacks, but it would also slow down the system to the point that users would look for ways to deactivate the mechanism. The security of the information is very important, but the costs are too high when emptying the memory caches reduces precious production time.
Attacks that use speculative-execution involve convincing the processor to speculate on a route that non-speculative-execution will not follow. For example, a kernel function may contain a limit check that will prevent the code from accessing beyond the end of an array, which will cause an error to be returned. An attack that uses the Spectre vulnerability will skip that check in a speculative way, accessing data that the code was written specifically not to access. The error return is a clue that maybe something inappropriate is happening, but by then, the damage will be done.
How to check if your Linux server is vulnerable to Spectre CPU bugs
Spectre & Meltdown Checker is a shell script that checks for the following Intel/AMD/ARM and other CPUs for bugs:
- CVE-2017-5753: bounds check bypass (Spectre Variant 1). You need to recompile software and kernel with a modified compiler that introduces the LFENCE opcode at the proper positions in the resulting code. The performance impact of the mitigation is negligible.
- CVE-2017-5715: branch target injection (Spectre Variant 2). The performance impact of the mitigation depending on your CPU.
- CVE-2017-5754: rogue data cache load (Meltdown). You must install updated kernel version with PTI/KPTI patches. Updating the kernel is enough. The performance impact of the mitigation is low to medium.
spectre-meltdown-checker.sh is a simple shell script to find out if your Linux kernel (installation) is vulnerable against the 3 “speculative execution” CVEs.
Installation
The script must be run as root user. You can view source code below. Use the wget command or curl command to grab the source code on your Linux box:
$ cd /tmp/
$ wget https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh
OR
$ git clone https://github.com/speed47/spectre-meltdown-checker.git
Sample outputs:
Cloning into 'spectre-meltdown-checker'...
remote: Counting objects: 155, done.
remote: Compressing objects: 100% (20/20), done.
remote: Total 155 (delta 18), reused 21 (delta 10), pack-reused 125
Receiving objects: 100% (155/155), 49.78 KiB | 145.00 KiB/s, done.
Resolving deltas: 100% (88/88), done.
How to check Linux for Spectre and Meltdown vulnerability
Run the script as root user using sudo command or su command:
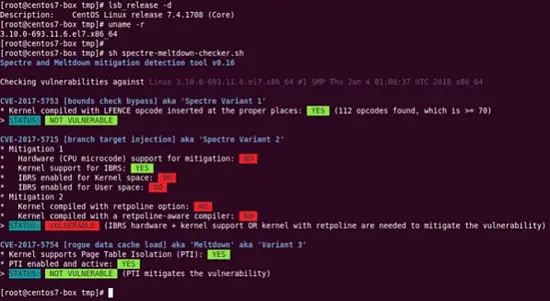
$ sudo sh spectre-meltdown-checker.sh
Sample outputs from Ubuntu Linux desktop:
Another output from my CentOS 7.x server where Meltdown/Spectre v1 was patched with Kernel:
$ sudo sh spectre-meltdown-checker.sh
How to install/update Intel microcode firmware on Linux?
A microcode is nothing but CPU firmware provided by Intel or AMD. The Linux kernel can update the CPU’s firmware without the BIOS update at boot time. Processor microcode is stored in RAM and kernel update the microcode during every boot. These microcode updates from Intel/AMD needed to fix bugs or apply errata to avoid CPU bugs. This page shows how to install AMD or Intel microcode update using package manager or processor microcode updates supplied by Intel on Linux.
How to find out current status of microcode
Run the following command as root user:
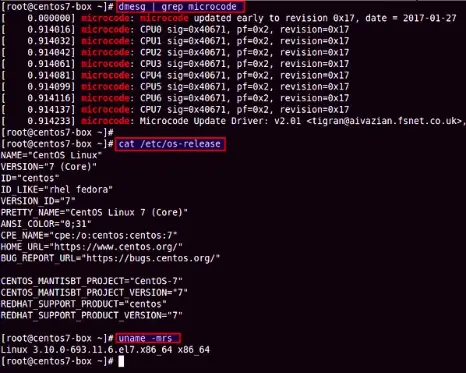
# dmesg | grep microcode
Sample outputs:
How to install Intel microcode firmware on Linux using a package manager
Tool to transform and deploy CPU microcode update for x86/amd64 comes with Linux. The procedure to install AMD or Intel microcode firmware on Linux is as follows:
- Open the terminal app
- Debian/Ubuntu Linux user type: sudo apt install intel-microcode
- CentOS/RHEL Linux user type: sudo yum install microcode_ctl
The package names are as follows for popular Linux distros:
- microcode_ctl and linux-firmware – CentOS/RHEL microcode update package
- intel-microcode – Debian/Ubuntu and clones microcode update package for Intel CPUS
- amd64-microcode – Debian/Ubuntu and clones microcode firmware for AMD CPUs
- linux-firmware – Arch Linux microcode firmware for AMD CPUs (installed by default and no action is needed on your part)
- intel-ucode – Arch Linux microcode firmware for Intel CPUs
- microcode_ctl, linux-firmware and ucode-intel – Suse/OpenSUSE Linux microcode update package
Warning: In some cases, microcode update may cause boot issues such as server getting hang or resets automatically at the time of boot. Do it at your own risk.
Examples
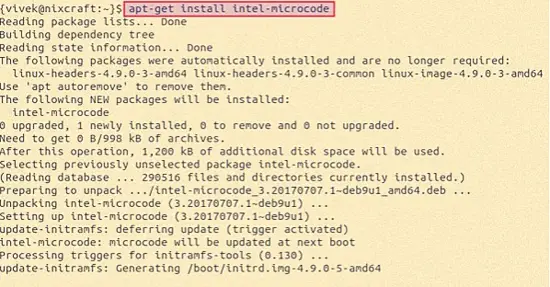
Type the following apt command/apt-get command on a Debian/Ubuntu Linux for Intel CPU:
$ sudo apt-get install intel-microcode
Sample outputs:
You must reboot the box to activate microcode update:
$ sudo reboot
Verify it after reboot:
# dmesg | grep 'microcode'
If you are using RHEL/CentOS try installing or updating the following two packages using yum command:
$ sudo yum install linux-firmware microcode_ctl
$ sudo reboot
$ sudo dmesg | grep 'microcode'
How to update/install microcode downloaded from Intel site?
Only use the following method when recommended by your vendor otherwise stick to Linux packages as described above. Most Linux distro maintainer update microcode via the package manager. Package manager method is safe as tested by many users.
How to install Intel processor microcode blob for Linux (20180108 release)?
Visit AMD or Intel site to grab the latest microcode firmware. First extract it using the tar command:
$ mkdir firmware
$ cd firmware
$ tar xvf ~/path/to/file/microcode-20180108.tgz
$ ls –l
Sample outputs:
Make sure /sys/devices/system/cpu/microcode/reload exits:
$ ls -l /sys/devices/system/cpu/microcode/reload
You must copy all files from intel-ucode to /lib/firmware/intel-ucode/ using the cp command:
$ sudo cp -v intel-ucode/* /lib/firmware/intel-ucode/
You just copied intel-ucode directory to /lib/firmware/. Write the reload interface to 1 to reload the microcode files:
# echo 1 > /sys/devices/system/cpu/microcode/reload
Update an existing initramfs so that next time it get loaded via kernel:
$ sudo update-initramfs -u
$ sudo reboot
Verifying that microcode got updated on boot or reloaded by echo command:
# dmesg | grep microcode
That is all. You have just updated firmware for your Intel CPU.