WAF Simulator: Transforming DevSecOps Workflows
Fastly has introduced a WAF Simulator, designed to make it easier for Fastly customers to test and validate rules. Unlike the conventional method, which requires creating and sending simulated attack traffic to your website following the implementation of a rule, our WAF simulator allows for validation of rules through Fastly's API. This streamlined approach offers several significant advantages in testing your WAF rules.
Improved accuracy: You can craft specific requests that trigger the rule you're testing, and verify the rule is blocking or tagging the request as expected.
Safe, controlled testing: Review how real traffic is handled in a simulated environment rather than experimenting with how altered rules handle potentially malicious traffic in your live production environment.
Efficient workflows: You can test a rule quickly and easily, without having to set up complicated testing infrastructure, reducing the resources required, both technological and human.
Repeatability: It might take several times to get a rule working as expected or requires continuous verification. Test as often as needed to verify that the rule is working correctly.
Unified integration: Users no longer need to switch between different systems or tools to complete their testing; everything they need is available in one place.
Now from deployment to testing, and integration with existing tools, Fastly provides a comprehensive suite of features designed to streamline your DevSecOps workflows, making it easier, and more effective to secure your organization.
Flexible deployments
It all starts with deployments. Fastly supports a variety of installation and deployment options. We’re infrastructure agnostic – we integrate into newer infrastructure like containers, Kubernetes, and service meshes. And we also integrate with network elements like API gateways and Edge. These integrations support a distributed collection of web app and API traffic across architectures that exist both on-premises and in the cloud, and most of our customers are already automating these deployments today.
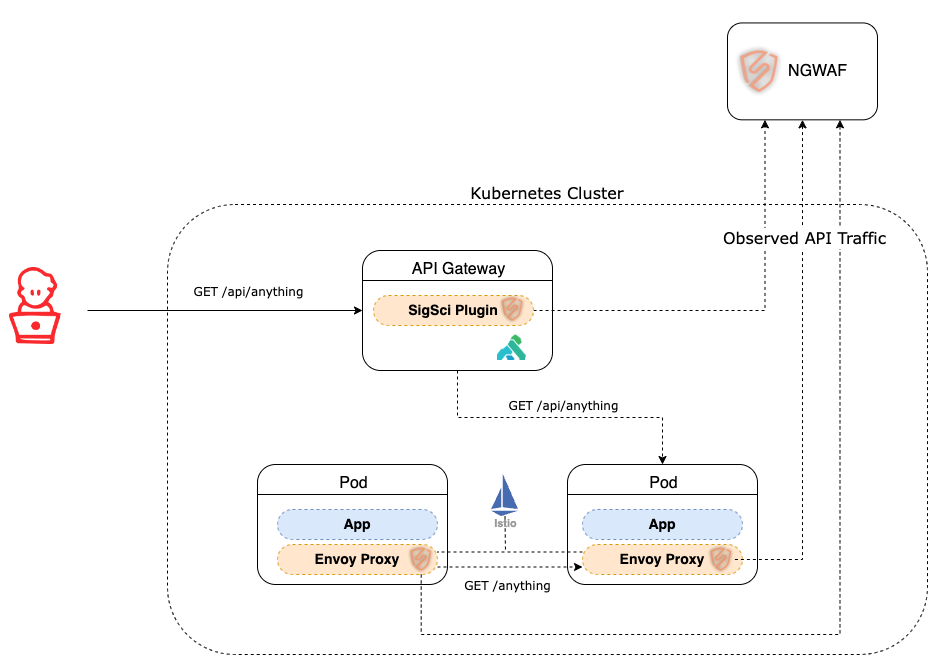
Shared responsibility model
The modern approach to security is a “shared responsibility” model…Siloed thinking is replaced by shared responsibility for security tasks during all phases of the delivery process. This can even include managing WAF rulesets and alerts for services you build.
Fastly’s Next-Gen WAF (NGWAF) is built for a shared responsibility model. Security teams or administrators can have high-level governance at the organization (corp) level and the ability to create centrally established policies and rulesets applied to each site. This gives teams the ability to configure and manage the rulesets for their apps and services they build while administrators still have overarching visibility.
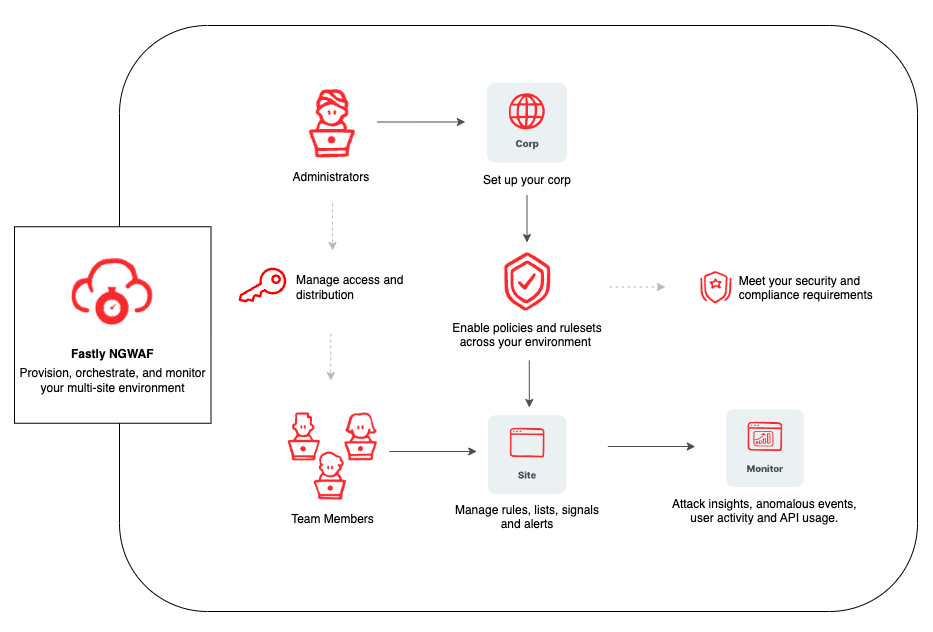
Terraform support
We built the NGWAF with an API-First approach, so it enables you to automate tasks that are traditionally performed manually in the management console. An example of this is through the use of our Terraform provider. Terraform is HashiCorp's infrastructure as a code tool. It’s one of the most popular tools used by DevOps teams to automate infrastructure tasks. This includes resources on AWS, GCP, and Azure among many others. It’s used to provision, update, and destroy infrastructure resources through a provider's API.
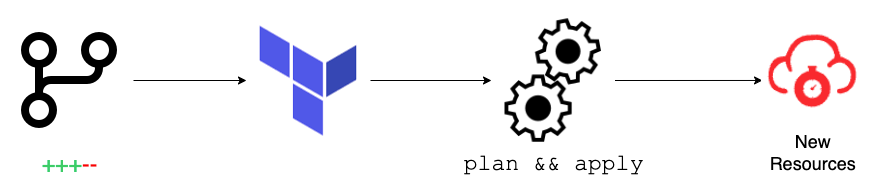
For instance, a customer with a large portfolio of applications can have 100s or even 1000s of sites, and each site can have numerous custom WAF rulesets, lists, and signals that can be untenable. Terraform provides a structured, version-controlled way to manage these configurations, reducing time and resources spent managing a WAF.
Figure 4 illustrates an example Terraformed site rule that matches and tags a request with a path in a sensitive account API endpoint list.
resource "sigsci_site_rule" "sensitive_account_api" {
site_short_name = var.site_name
type = "request"
group_operator = "all"
requestlogging = "sampled"
enabled = true
reason = "monitor sensitive account api endpoints"
expiration = ""
conditions {
type = "single"
field = "path"
operator = "inList"
value = sigsci_site_list.sensitive_account_api.id
}
actions {
type = "addSignal"
signal = sigsci_site_signal_tag.sensitive_account_api.id
}
}WAF simulator
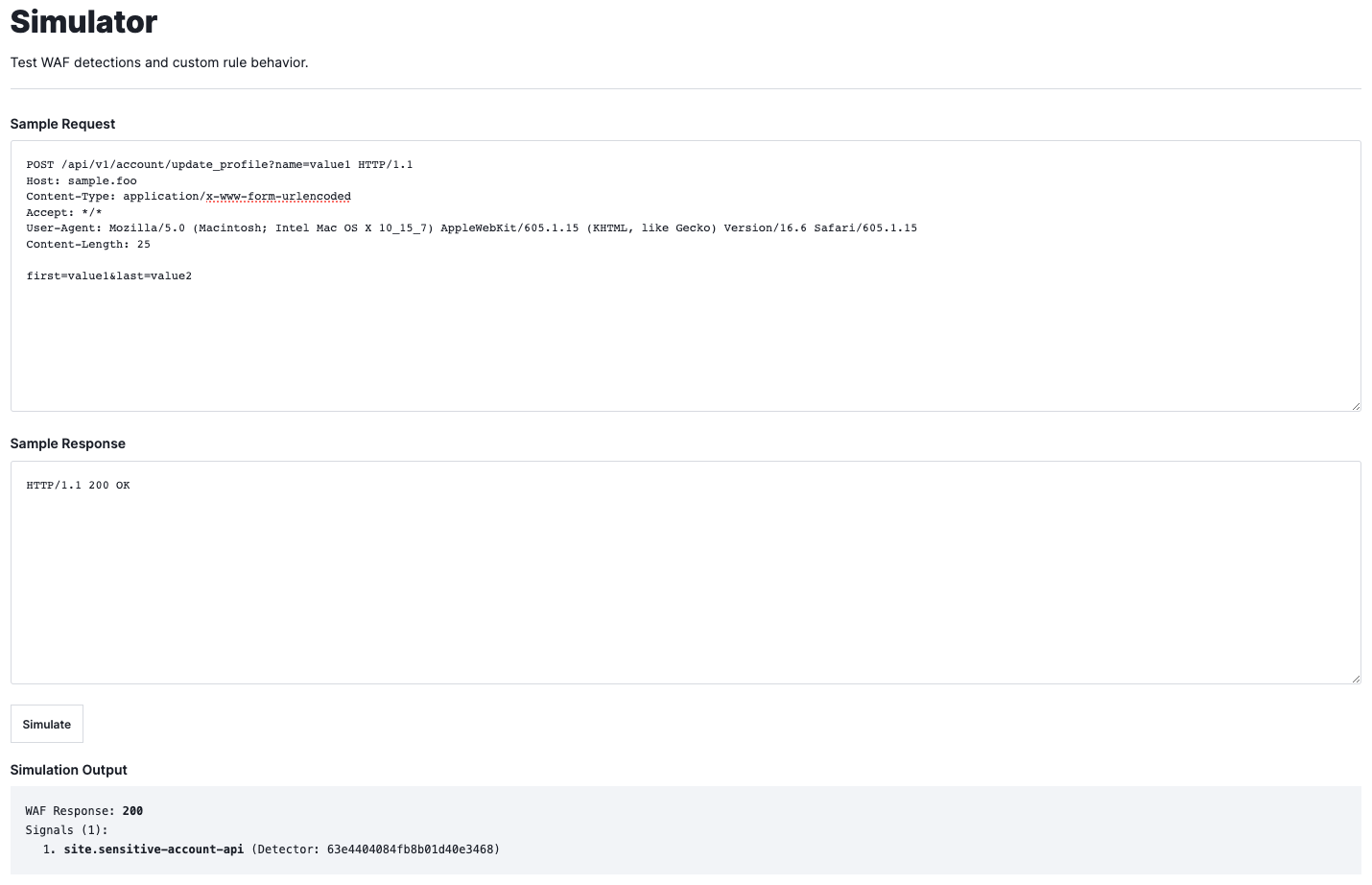
Once a rule has been created, a best practice is to validate that the rule performs as expected. Testing a rule is important because it helps ensure that the WAF continues to function properly over time, even as the application it’s protecting changes and evolves. When you add new rules, change existing rules, or make changes to the application the WAF is protecting, these tests help ensure that the changes don’t introduce new bugs or regressions that weaken your protection. In addition, many organizations are subject to compliance requirements, and regular testing can help demonstrate that you are meeting the required standards.
Fastly’s WAF simulator, allows Fastly customers to validate rules directly against our API without needing to switch between different systems or tools to complete their testing. Customers have the option to test and validate rules within the user console or they can leverage the API for integration into their CI/CD pipelines. Figure 5 illustrates testing a site rule in the console that matches and tags a request with a path in a sensitive account API endpoint list.
Integrations
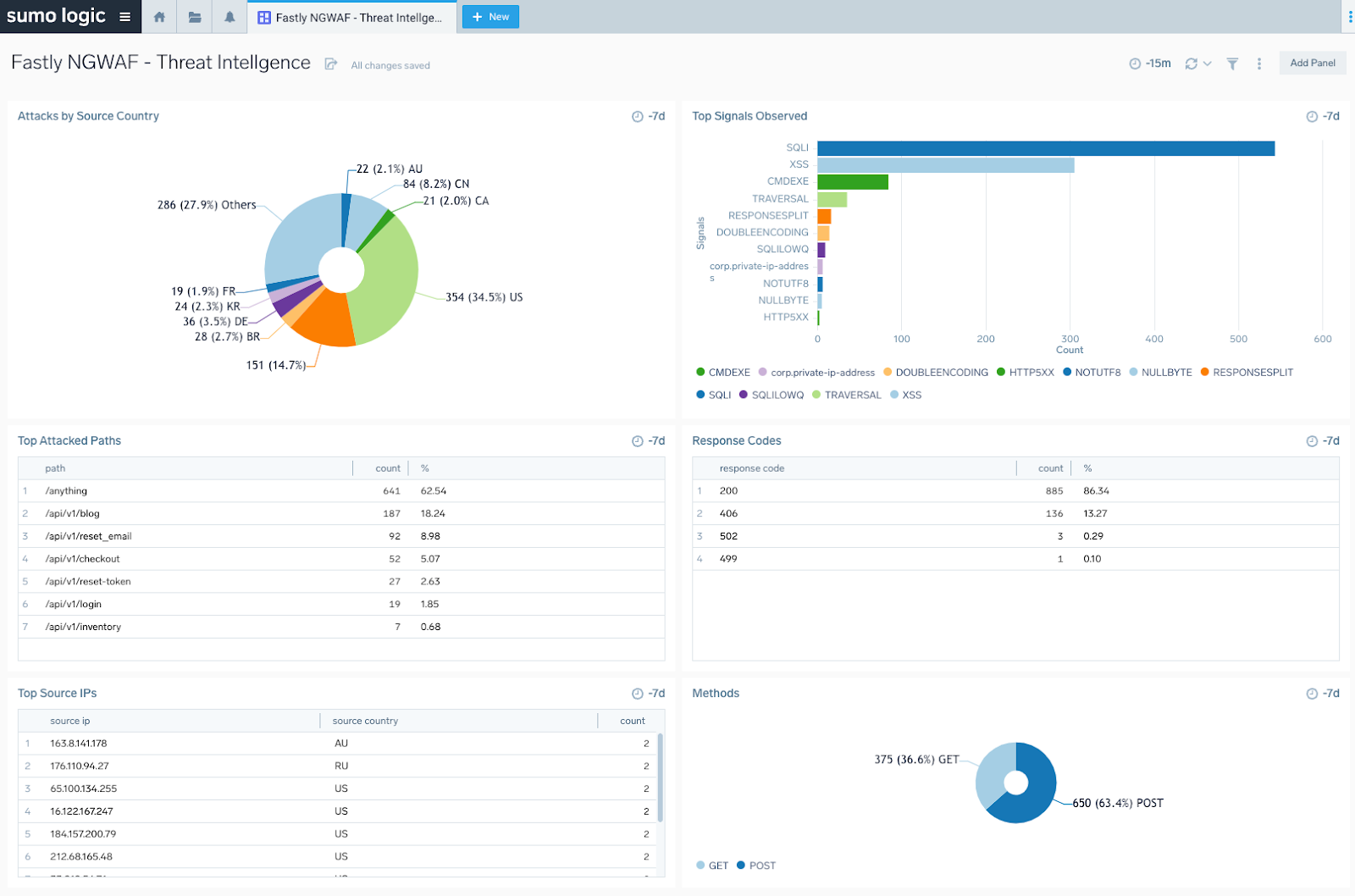
Third-party integrations are key components of any DevSecOps workflow. Teams can be more productive when they have to do less context-switching and manage fewer dashboards. Workflows often involve multiple tools and services and third-party integrations help connect those tools and services together – this can include notification and ticketing to ensure events are tracked and managed, and integrations used to pull NGWAF logs into a SIEM. NGWAF logs contain attempted attacks, known threats, and suspicious activity, which can be used to augment security incident response, as demonstrated in Figure 6 below. Some organizations prefer to centralize their data in an SIEM which can more easily help identify and respond to security threats, detect anomalies and perform forensic investigations.
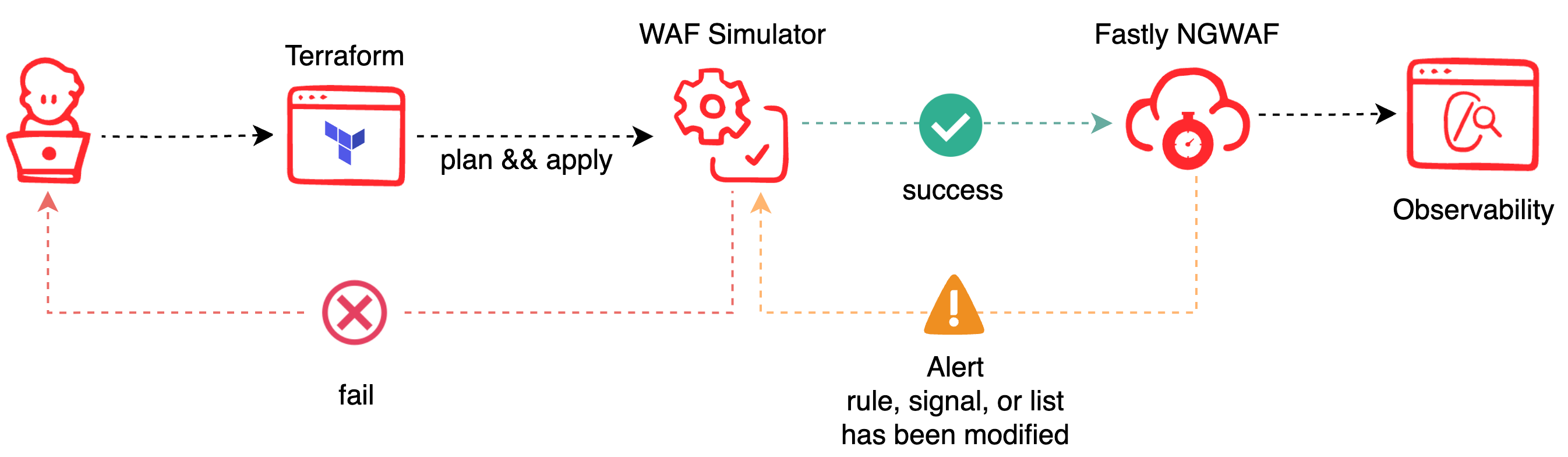
Automating Your DevSecOps Workflow
The NGWAF is fundamentally designed with DevOps and DevSecOps professionals in mind. Its key features enable automated workflows into CI/CD pipelines, compatible with a wide array of technology stacks. This includes automated deployments, using Terraform for provisioning rules, continuous validation of rules using the WAF simulator, and end-to-end visibility via the management console or your preferred third-party tool.
From deployment to rule validation and comprehensive monitoring, Fastly’s NGWAF fortifies security and simplifies management, ensuring that your services remain robust, secure, and ahead in the rapidly evolving digital landscape. Interested in seeing what the NGWAF can do for your business? Unlock the power of DevOps-friendly security with Fastly.
Additional resources:

