How our customers can protect themselves against the Apache HTTP Server vulnerability
What you need to know:
- The recent Apache HTTP Server vulnerability (CVE-2021-41773) is reportedly being exploited in the wild. While it is an unauthenticated and remotely exploitable vulnerability, it requires specific conditions for servers to be vulnerable.
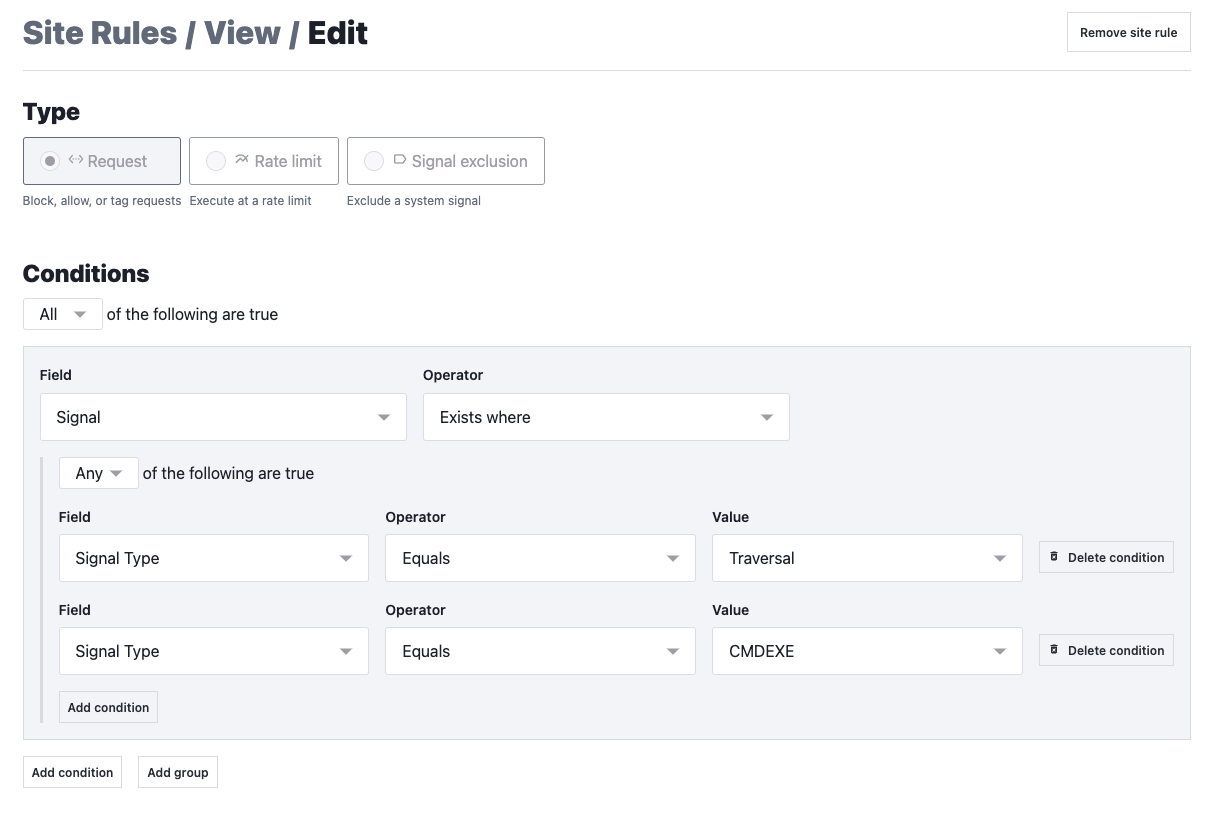
- Fastly already detects this vulnerability (TRAVERSAL & CMDEXE). For extra precaution, we recommend our next-gen WAF (formerly Signal Sciences) customers create a rule to block exploitation (see below).
- There is a patch available from Apache that should be applied immediately to any Apache HTTP Server running 2.4.49.
CVE-2021-41773 is a path traversal and file disclosure vulnerability facilitating remote code execution in Apache HTTP Server 2.4.49 (only this version). It allows a remote user to gain unauthorized access to restricted directories and potentially execute remote code to gain control over the target system.
What’s the impact?
This vulnerability only impacts Apache HTTP Server (aka httpd) version 2.4.49 with the default access control configuration — “require all denied” — disabled. Although that means attackers need to find servers with those specific conditions to exploit it, data from Shodan suggests that there are over 100,000 servers matching this criteria.
If an attacker exploits this vulnerability as an unauthenticated user, they could gain full access to the system. From there, they could read or exfiltrate sensitive information or, in a worst case scenario, seize control of the system. Additionally, exploiting this vulnerability could leak the source of interpreted files like CGI scripts, which can contain juicy resources like credentials and keys that you probably don’t want attackers accessing.
Yes, but...
Version 2.4.49 of httpd has only been around for two weeks, so enterprises who haven’t updated their servers yet won’t be affected by this vulnerability. This reflects a rare case of procrastination paying off — but treat it as luck rather than a security strategy.
The better takeaway is that keeping secure defaults (like “require all denied” being enabled) in your servers is a sound default security strategy.
Why it’s cool
Due to better engineering practices over the past few years, Path Traversal and RCE vulnerabilities are becoming less common in the wild. Therefore, this vulnerability offers a fittingly spooky vibe during the month that offers us both Halloween and Cyber Security Awareness.
Digging deeper
The path traversal fix previously made in 2.4.49 introduced a check for the presence of path traversal characters (like “../”). Unfortunately, the fix didn’t assume the possibility of an attacker providing the percent-encoded versions of these characters. The new fix that went into httpd version 2.4.50 now checks for “%2E” and “%2e,” which is the encoded representation of the dot (“.”) — meaning attackers can no longer use this clever loophole for path traversal.
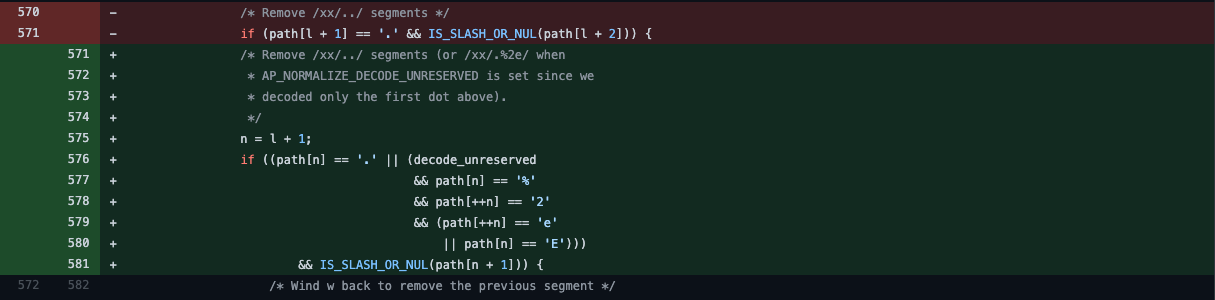
It was found that the fix for CVE-2021-41773 in Apache HTTP Server 2.4.50 was insufficient. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives.
What you should do
Anyone with Apache HTTP servers using version 2.4.49 should ensure that the “require all denied” configuration is enabled and, even better, upgrade to version 2.4.51 that includes the fix for this vulnerability (and the one introduced in 2.4.50).
Fastly already detects this vulnerability via the TRAVERSAL & CMDEXE signals. If you’re a next-gen WAF customer, you can also follow the steps below to enable a site rule to protect yourself from exploitation of CVE-2021-41773.
Navigate to the Site Rules and click Create a site rule. From there you can fill out the conditions as follows: